Single Sign On Configuration
Beeceptor offers support for SAML 2.0-based Single Sign-On (SSO) login, allowing seamless integration with prominent identity management tools like Google Workspace, Azure Active Directory, Okta, among others, to delegate authentication for your users.
This feature is available with the Enterprise plan.
Azure Active Directory
Enabling Azure Active Directory (Azure AD) for Beeceptor login involves the following steps in the new Azure Management Console.
- You need to access the Microsoft Azure Management Console and navigate to Azure Active Directory in the navigation pane.
- Select 'Enterprise Applications' and follow the provided tutorial for setup.
- Follow the below tutorial for complete setup.
Beeceptor Configuration Details
For configuring the Beeceptor details in Azure SAML application setup, please use the following required attributes:
- Identifier (Entity ID):
beeceptor.com - Reply URL (Assertion Consumer Service URL):
https://app.beeceptor.com/auth/identity-provider/callback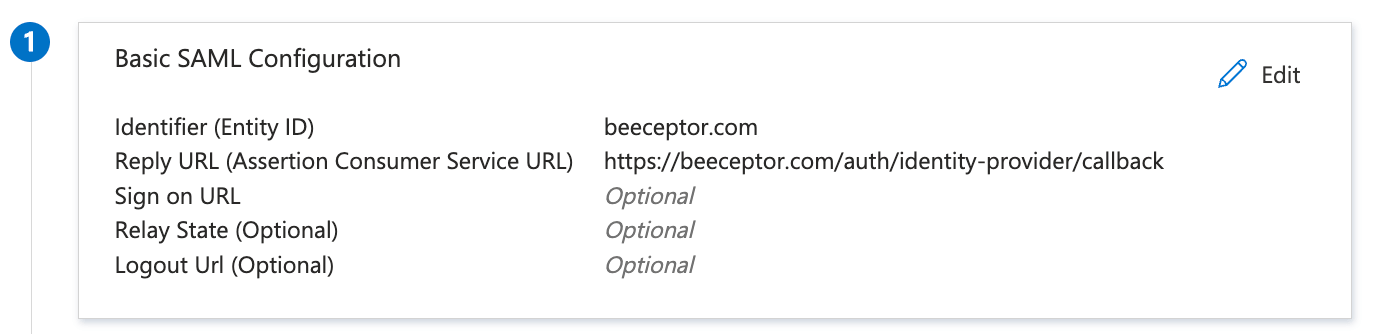
Azure AD App Details
Map The Claims
To ensure Beeceptor receives attributes/claims from Azure AD, map the following attributes:
- Update
Unique User Identifiertouser.mail. - Create
displayNameas new claim, and map it touser.displayname.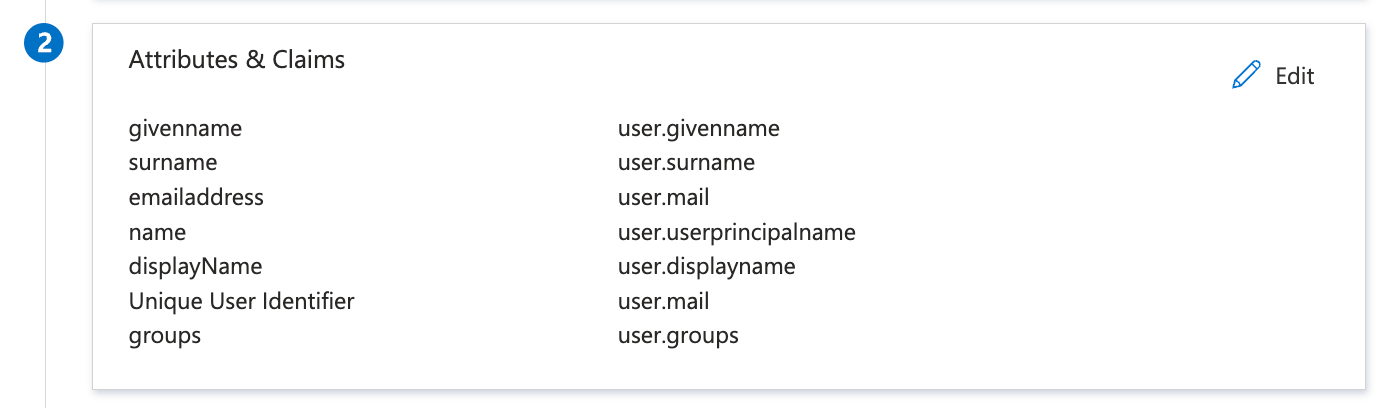
- You can optionally add
Groupsinformation to the claim for Beeceptor to enable a deeper access control.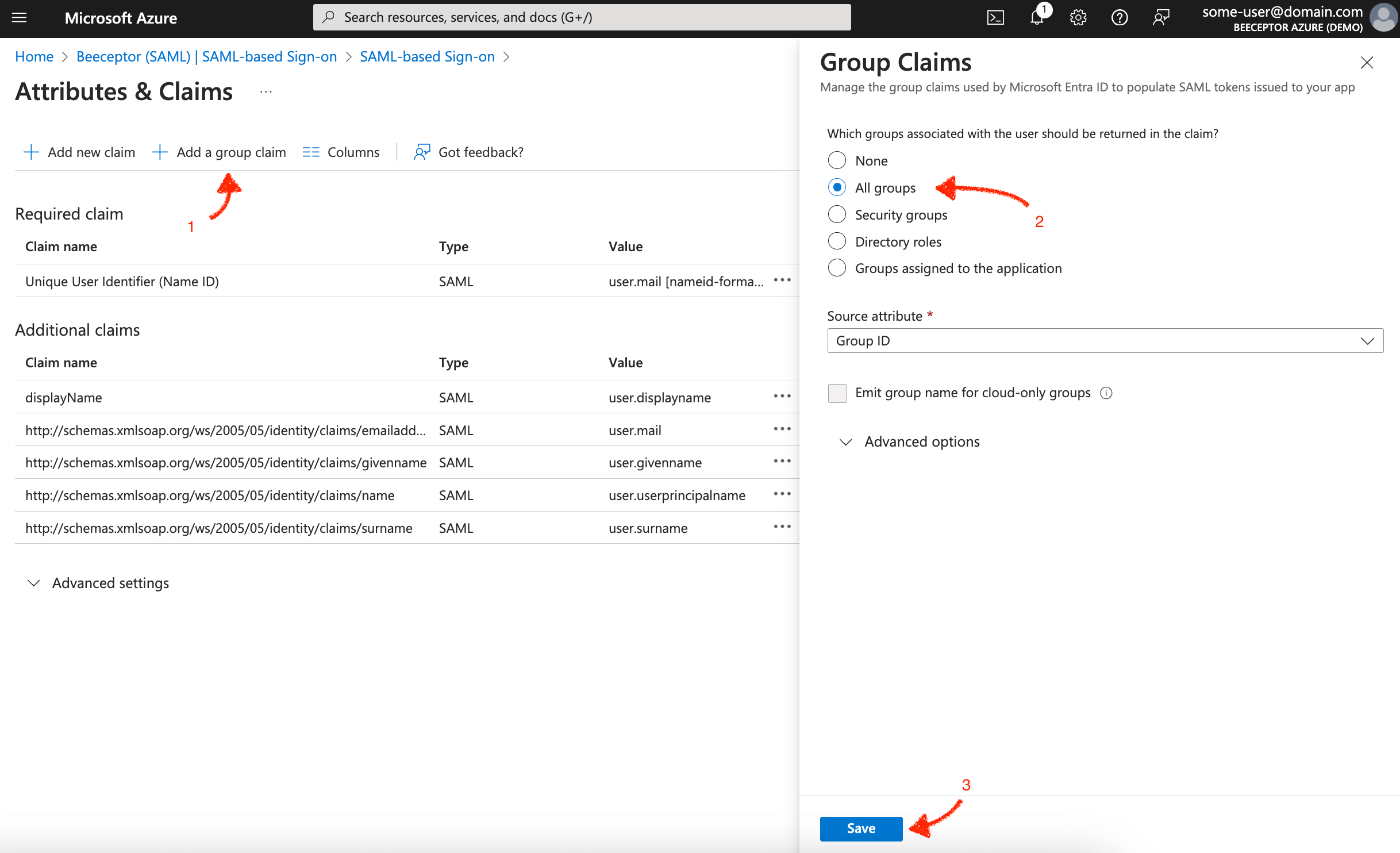
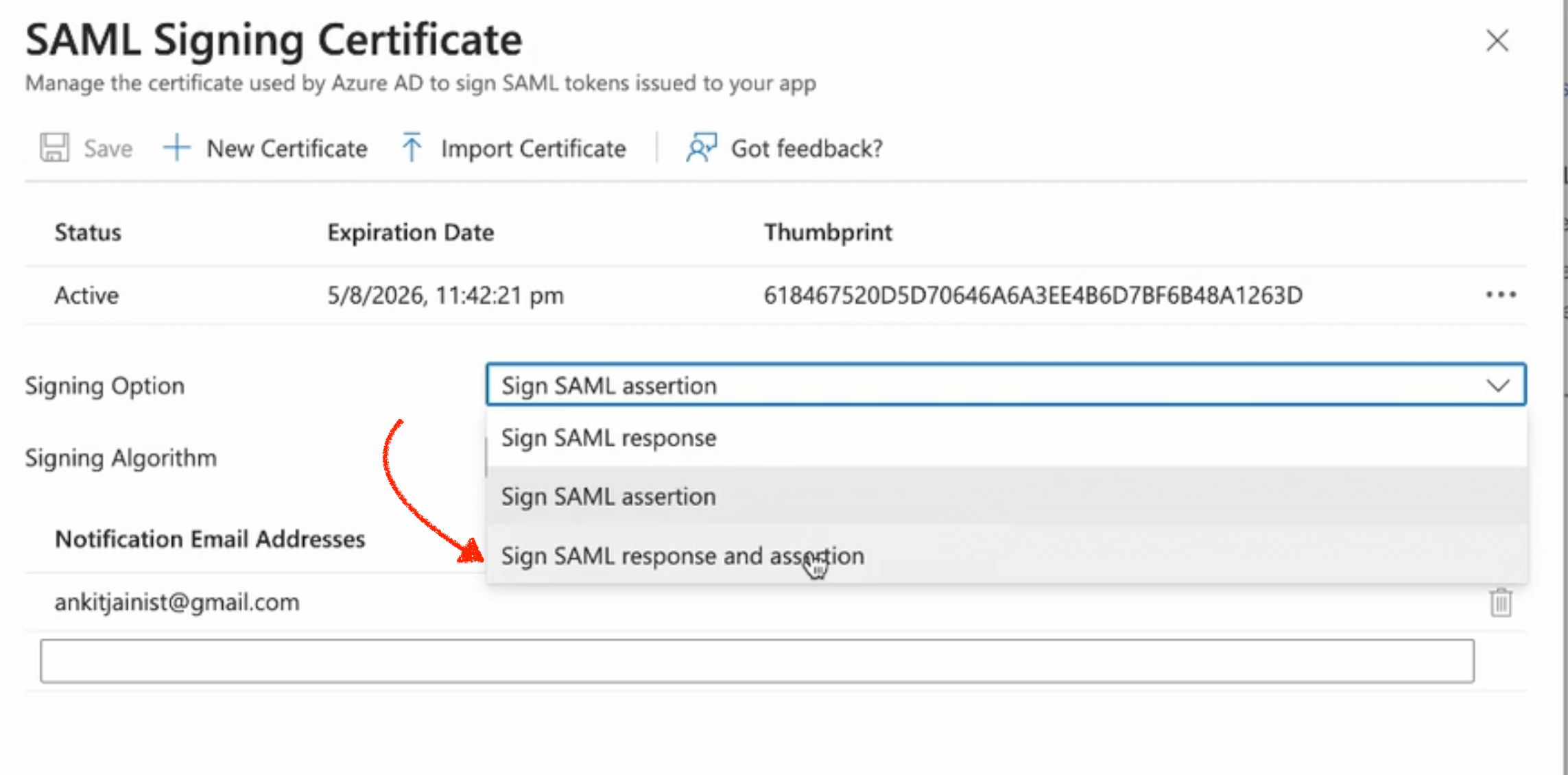
Response Signing
Beeceptor expects response as well as assertion signed. Use the following steps to enable it:
- Navigate to 'SAML Certificates' (step 3 on the same page) and click Edit.
- Within the 'Signing Option' section, opt for 'Sign SAML Response and Assertion'.
- Save your changes
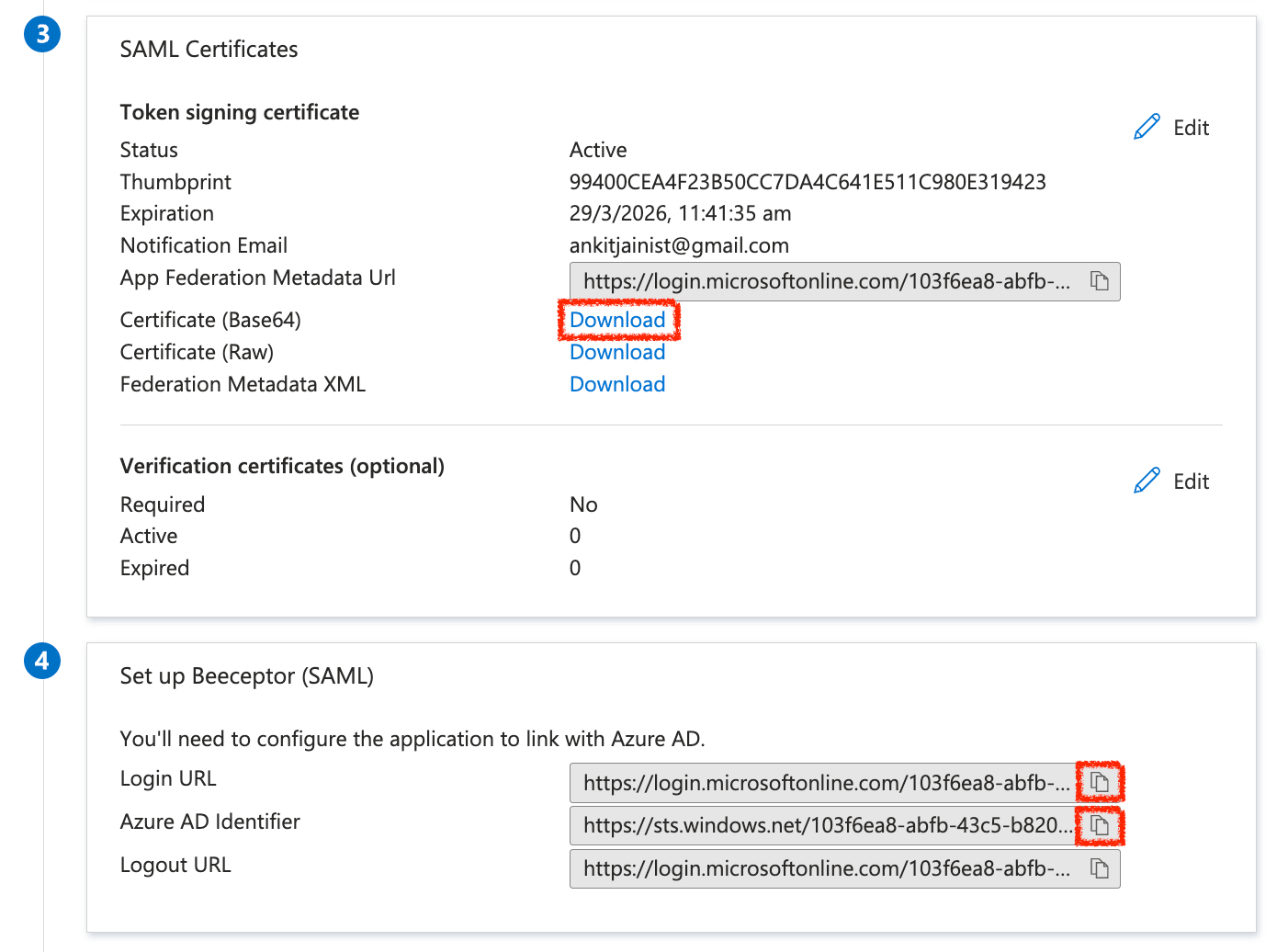
Share With Beeceptor
To proceed further, provide the following information to Beeceptor support team:
- Your organization's email domain
- The Base64 encoded certificate
- Login URL
- Azure AD Identifier.
Optional Configuration
Add Logo
Additionally, to enhance the user experience, you can add the Beeceptor logo so that users can easily recognize the application. The Beeceptor logo is available at the following links:
- Large bee logo https://cdn.beeceptor.com/assets/images/beeceptor-large-bee.png
- Small bee logo https://cdn.beeceptor.com/assets/images/logo-beeceptor.png
Assign Users Using Groups
Ensure to assign users or groups to the Beeceptor application. Only the assigned users will be able to see the Beeceptor app icon under "My Applications."
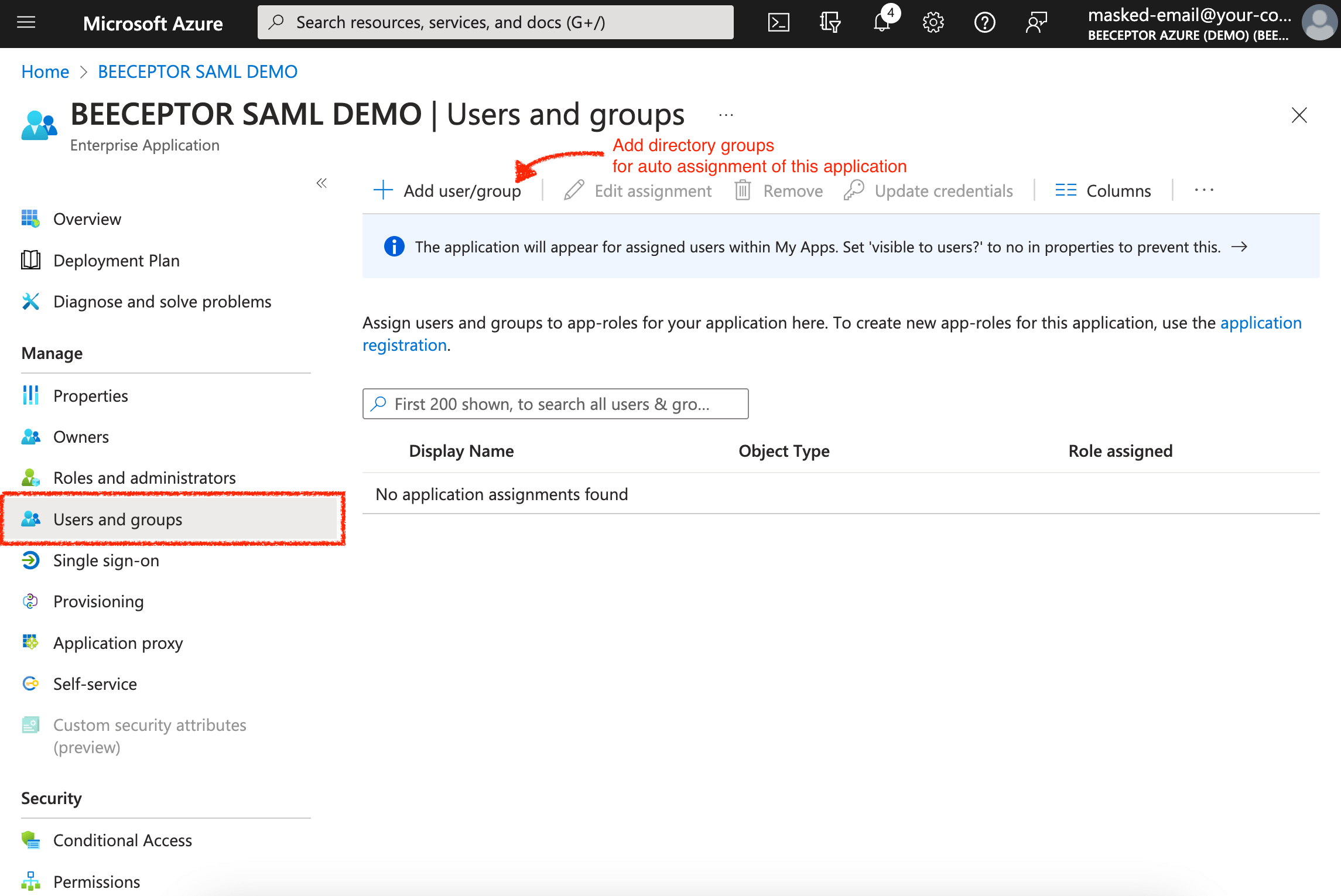
- Please note that Beeceptor does not support the syncing of Groups from Azure AD to Beeceptor. Permissions and roles are managed within Beeceptor per endpoint.
Test The Integration
The Beeceptor Support Team will complete the configuration for your domain. You can initiate testing once the support team confirms the setup. Just click the 'Test' button to validate the end-to-end integration.
It's worth noting that Beeceptor will automatically provision a user on their first login attempt. Users can log in to Beeceptor via SAML in two distinct methods:
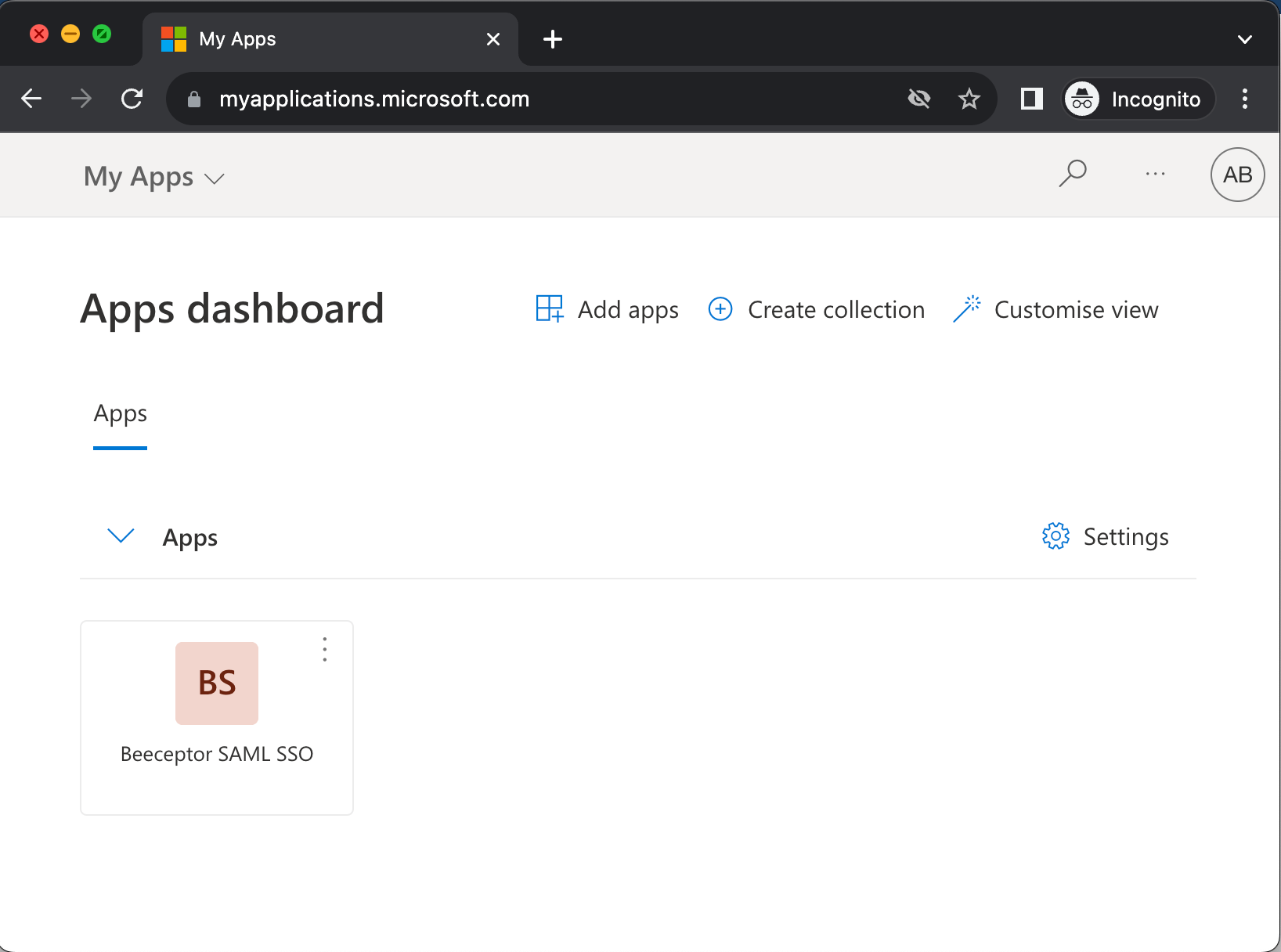
IdP Initiated Login
Within your Microsoft or Office 365 account, click on App Launcher, click on All Apps and you will be able to see Beeceptor app there.
SP (Beeceptor) Initiated Login
Your users are requested to utilize the following link to access Beeceptor's Single Sign-On (SSO):
https://app.beeceptor.com/auth/identity-provider
Google Workspace Directory
Beeceptor supports SAML based IdP initiated or SP initiate logins. Enabling Google Workspace for Beeceptor login involves the following steps in the Admin Console.
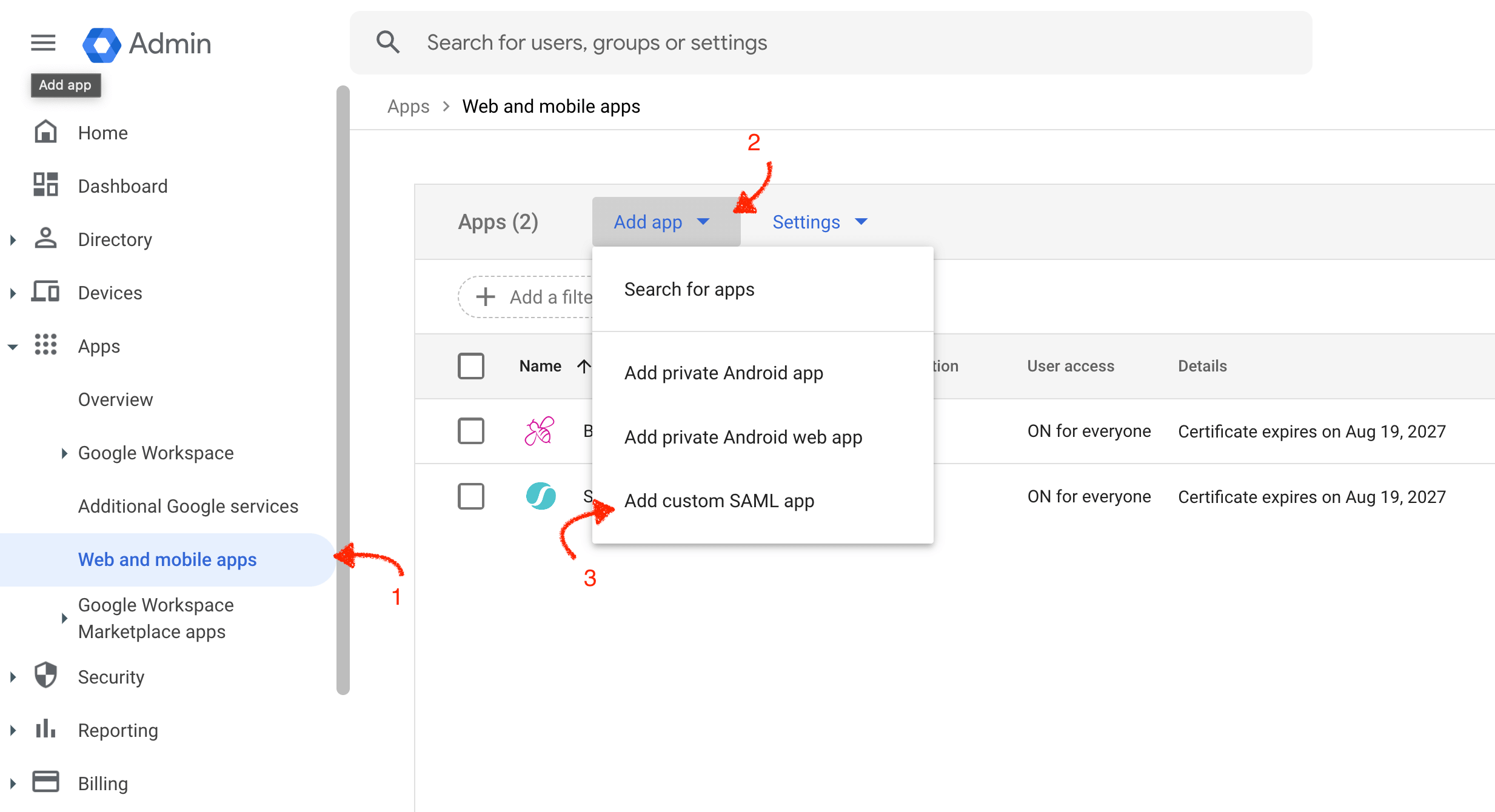
Open Apps Listing
- Open Admin Console.
- Navigate to Apps -> Web and mobile apps -> Add app -> Add custom SAML app
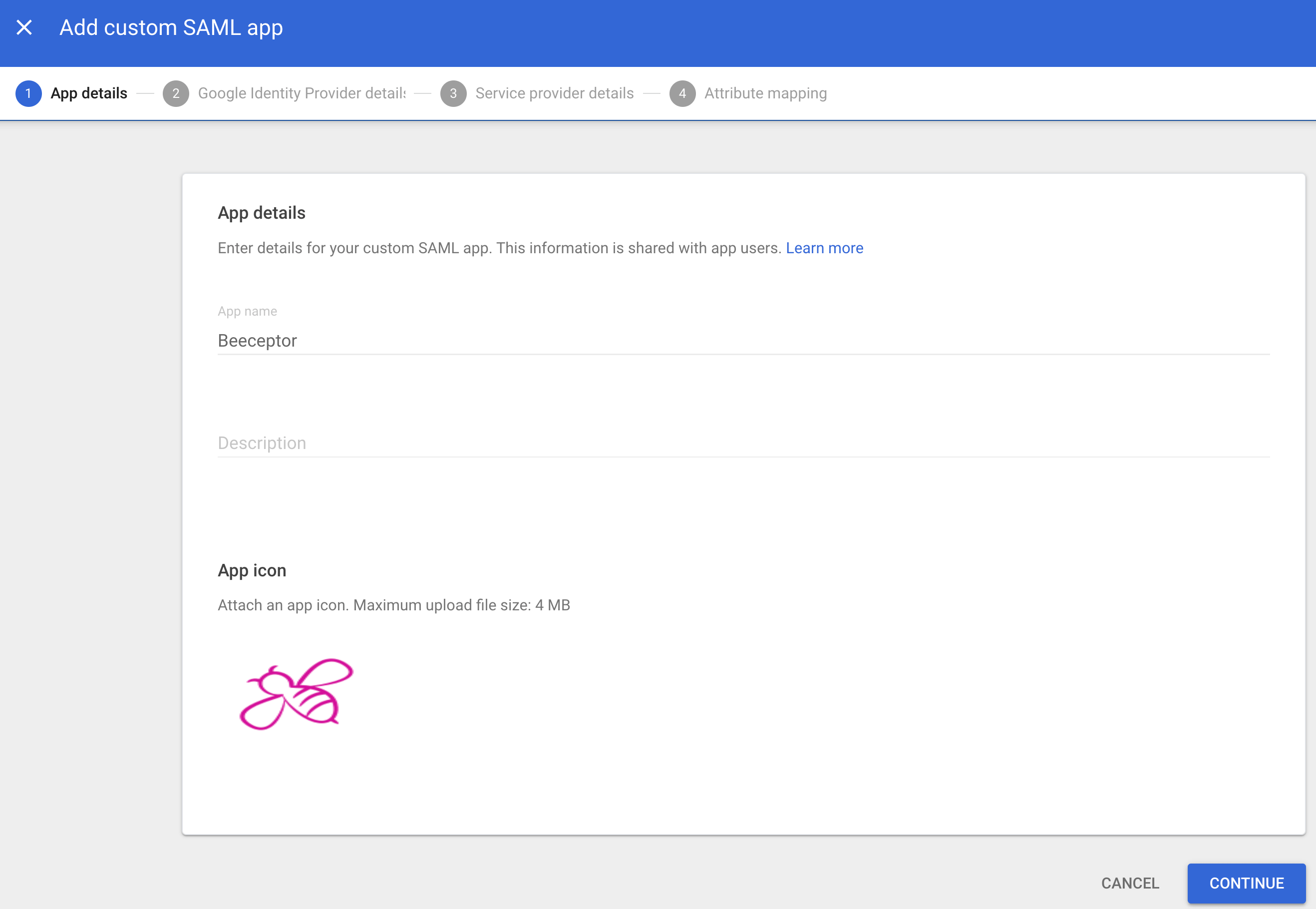
Creating A SAML App
You should give this application a name, say Beeceptor, and configure logo. Logo makes it easy for users to recognize the application. The Beeceptor logo is available at the following links:
- Large bee logo https://cdn.beeceptor.com/assets/images/beeceptor-large-bee.png
- Small bee logo https://cdn.beeceptor.com/assets/images/logo-beeceptor.png
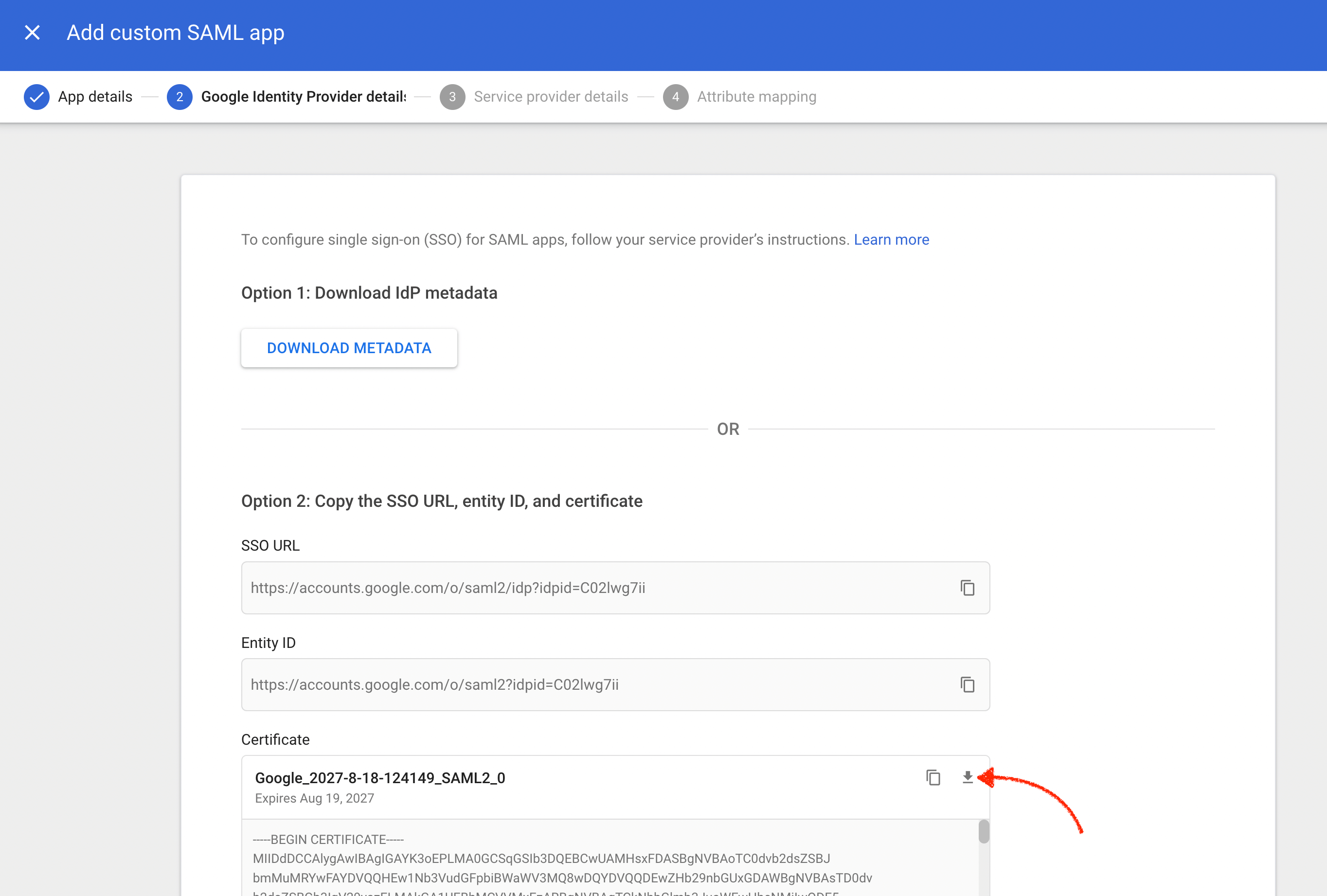
Google Identity Provider Details
Copy the following three details from this step and share with Beeceptor support team.
- SSO URL
- Entity ID (Identifier of the IdP)
- Certificate: Download the certificate file.
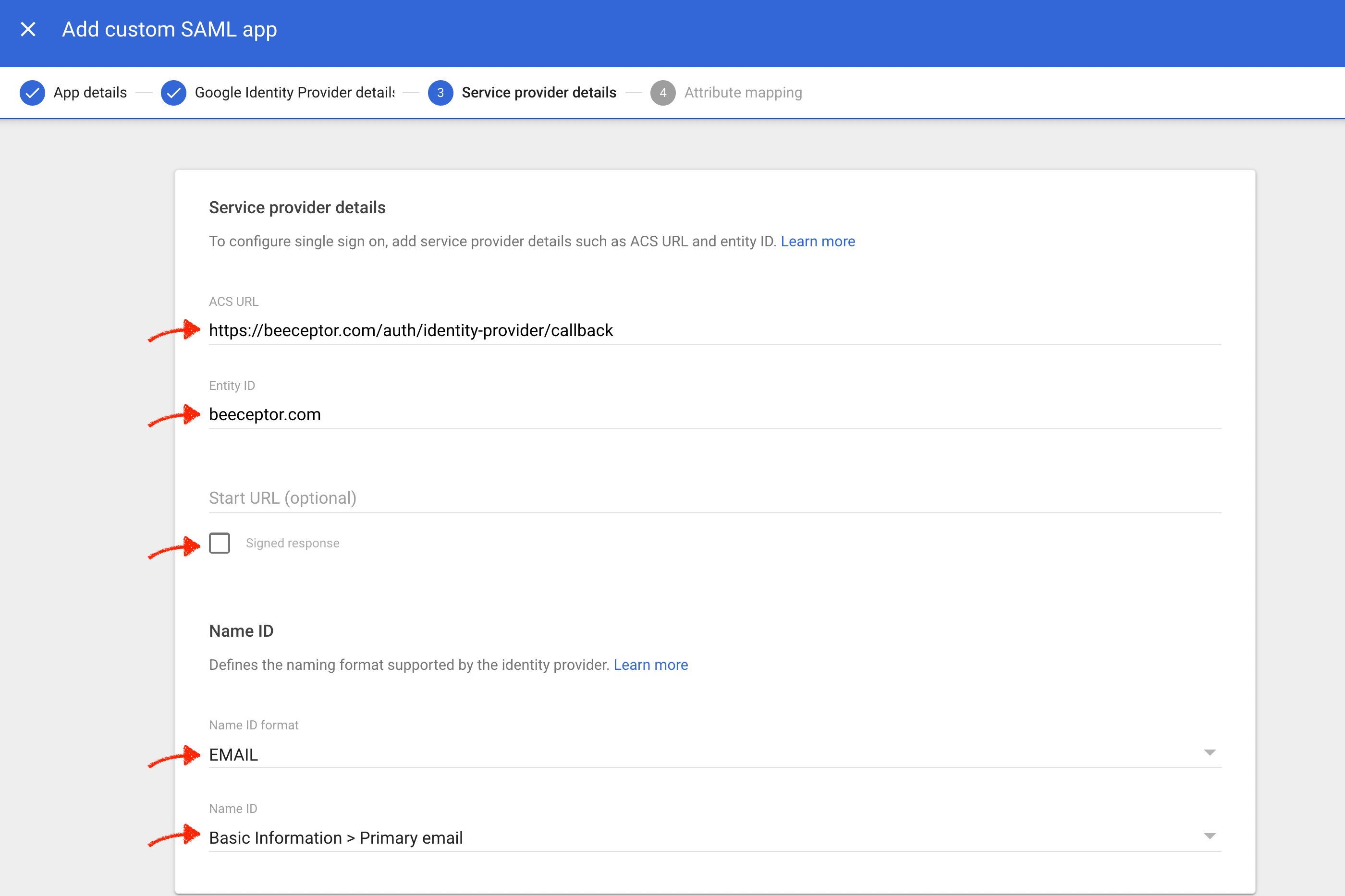
Service Provider Details (from Beeceptor)
Enter the following values as Beeceptor's SAML configuration:
- ACS URL (Assertion Consumer Service URL):
https://app.beeceptor.com/auth/identity-provider/callback - Entity ID (Identifier of the Service Provider):
beeceptor.com - Ensure that you tick the 'Signed Response' checkbox.
- Map
EMAILas Name ID attribute.
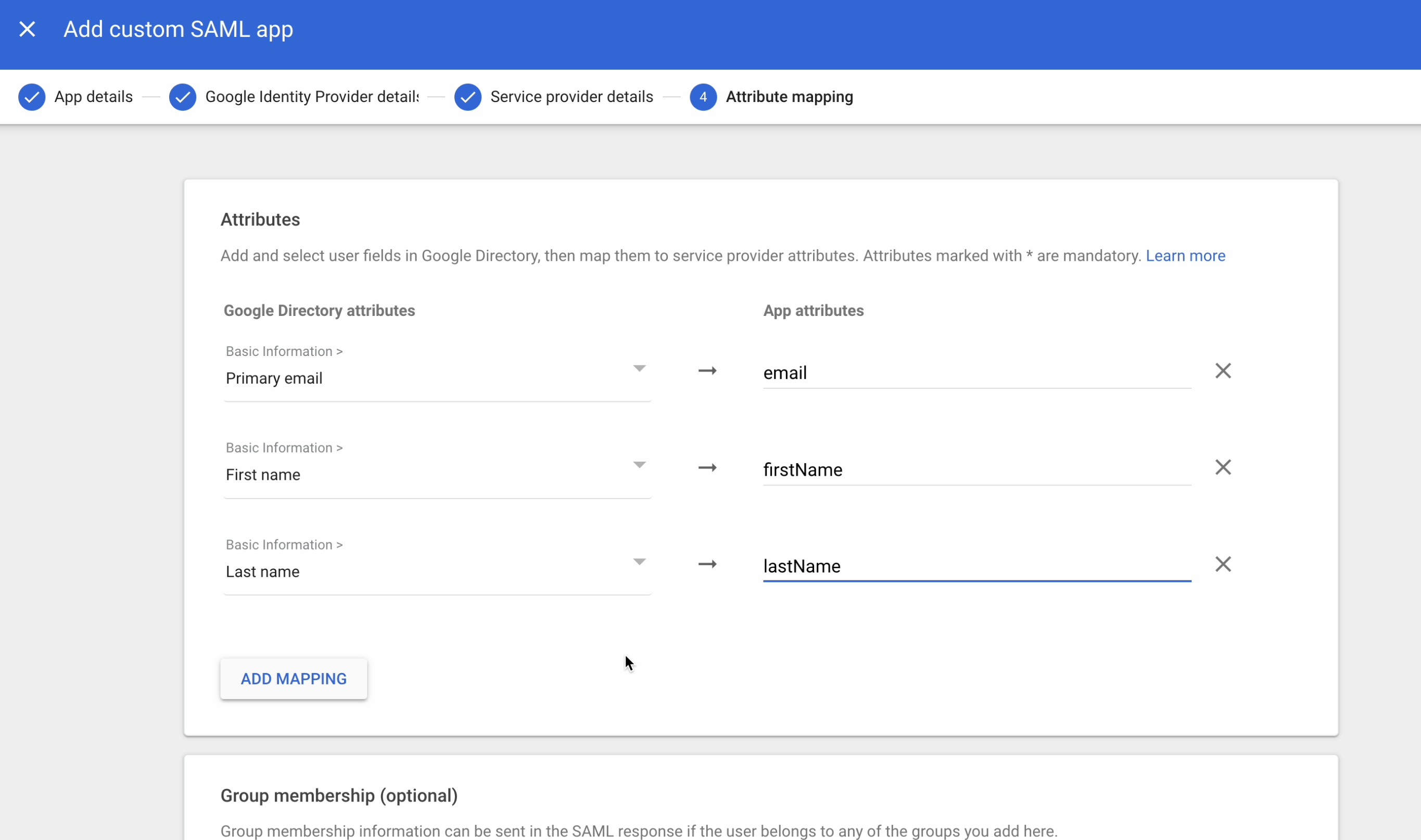
Attribute Mapping
Map the following three required attributes and complete the setup.
- Primary Email ->
email - First Name ->
firstName - Last Name ->
lastName
Test The Application
As a user, log in to your email, then click on the top apps icon. You'll find Beeceptor listed as an application. Click on the Beeceptor logo to access and log in to Beeceptor.